PLATO TALK #1 — Wonderful discussion sharing
 TOPIC: Talk about your views on privacy. Why is privacy important?
TOPIC: Talk about your views on privacy. Why is privacy important?
cherima
I believe that privacy is the product of human’s self-will and social development. It is an independent space established by a person, which can protect our spiritual world. When a person’s privacy is leaked, he will lose his sense of security, which may lead to huge problems in his life. People are the basic elements of society. The disclosure of a person’s privacy may not only affect him, but also his family, friends and colleagues. Privacy is closely linked with the current society. If the problem of privacy leakage occurs widely, it may lead to social instability.
Chopper
In the Internet era, data is a gold mine. Everyone participates in it, but it seems that all data does not belong to them. So the protection of private data is naturally important.
Facebook Now equipped with billions of these virtual identities, Facebook owns a treasure trove of data that it rents out to advertisers. To be clear, Facebook does not necessarily sell this data.
Instead, they use this data to create highly-accurate models, which marketers then target with ads. This is a double-edged sword (for us) as this data collection also contributes to Facebook’s ability to make its platform even more addicting, thus bringing in more attention.This process feeds into itself, creating the multi-billion dollar behemoths that we know today. On the off chance that you are still unaware, they have gotten really good at this. In 2020, Facebook brought in $85.96 billion in revenue, $84.2 billion of which was from advert
User-generated content (UGC) is the dominant model of the Internet. As you said, data brings a lot of profits to big companies, but we don’t share any of the profits, and they don’t even ask me , which reflects the importance of privacy protection. Let the data truly belong to the user.
there is another example of the importance of private data protection .The Year 2020, Finnish Psychology The cybercriminals behind a data breach at Vastaamo, a treatment facility, began blackmailing patients for hundreds each Euro and threatened to post their personal health data online. Hackers are said to have accessed 40,000 copies Vastaamo patients’ medical records and demanded a ransom of about 450,000 euros. The Tor site that the attacker is running The website posted 300 patient records, including therapists’ treatment records in addition to names and contact information. The disclosure of a person’s psychotherapy record can be even more damaging to patients, involving a person’s reputation, the person Relationships and work.
xiyu
Hello everyone.
I’d like to share with you some of my superficial understanding of privacy.
I want to talk about privacy from a technical point of view.
I think privacy can be divided into two levels, and basically I call it “static privacy”.
This is also the most common form of privacy, such as the transmission of information on untrusted links, in which information can be hijacked by anyone. If both sides of the communication are unwilling to disclose the specific content of the information, the simplest thing is of course to encrypt the information.
Symmetric encryption is one kind, but it can only realize the information exchange between two people. when the same person needs to interact with multiple people, it needs to manage multiple keys at the same time, so symmetric encryption appears to be “tightly coupled”.
Asymmetric encryption provides a more “loosely coupled” method, but this alone cannot resist man-in-the-middle attacks, so it is usually used with “signatures” to verify the identity of both sides of the interaction. in fact, this is the method that the blockchain can provide to us. At this point, if no processing is done, the identity and the privacy of the content will be bound together.
In some scenarios, people need to exchange confidential information anonymously. If man-in-the-middle attacks are considered, it is generally not easy for both parties to be anonymous. But it can ensure that the receiver does not know who the sender is. At this point, secret key exchange technology is combined with asymmetric encryption.
I call these scenarios “static privacy”, but what is “dynamic privacy”?
In fact, the existing cases of “dynamic privacy” scenarios are not common, but they are very useful. In fact, when we often talk about data rights in PlatON, we use what I call a “dynamic privacy” approach.
The important premise of confirming the right of data is the separation of the ownership and the right of use of the data. in the digital world, the replication of the data itself is very easy, so the previous data sale is basically an one-shot sale, when I sell the data in my hand. in theory, this data loses the value of being sold again.
In general, the value of the data can be extracted by mining algorithms, while different data mining methods may extract different values, so in theory, the data owner hopes to maintain the long-term value of the data. PlatON privacy computing technology system can actually bring this breakthrough.
In fact, the theoretical research in this field started very early, for example, algorithms such as FHE can support this implementation, but at present, the biggest problem is engineering implementation in applications. And the existing algorithms still have many defects in engineering landing, which may be the reason why we do not see too many applications of “dynamic privacy” at present. We hope that PlatON can bring important breakthroughs in this aspect in the future.
Privacy will be an important infrastructure for web3. In fact, in the past, the protection of user privacy was endorsed by large companies in the Internet field, and users have no ability to guarantee whether user data is used out of bounds.
But in the web3 scenario, although users have more freedom, they put forward higher requirements for privacy protection. An important concept of blockchain is “The code is law”, so privacy protection in the field of web3 needs decentralized privacy computing to ensure. This is an infrastructure-level requirement in the area of a blockchain.

 How to participate
How to participate
 Plato rewards
Plato rewards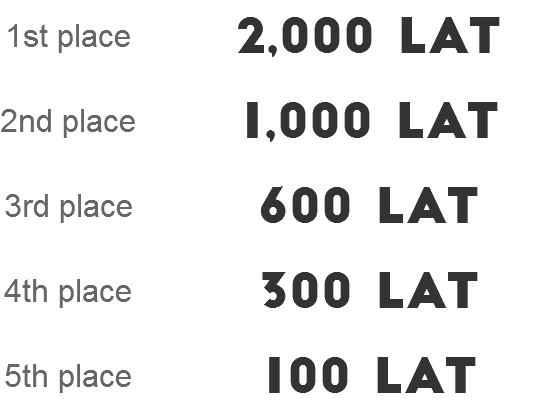
 Participation reward
Participation reward![]()

